A Guide to Modern Trust & Safety Strategy
Think of Trust & Safety as the immune system for any online platform. It's the combination of people, rules, and technology dedicated to keeping users safe from harm, and it's what allows a digital community to actually feel like a community.
Why Trust & Safety Is a Core Business Function

Picture an online platform as a bustling city. For it to truly prosper, its citizens need to feel safe. Trust & safety is the invisible infrastructure that makes this happen—it's the building codes, the police force, and the public health services all rolled into one. Without it, the city descends into chaos, and people start to leave.
Not long ago, many companies treated safety as a reactive measure, a clean-up crew to be called in after disaster struck. That mindset is a recipe for failure today. A proactive trust & safety strategy isn't just a "nice-to-have"; it's a non-negotiable part of building a sustainable business.
Building the Foundation for Growth
A smart trust & safety program does more than just put out fires. It actively builds the kind of user loyalty and brand reputation that fuels real growth. When people feel safe, they engage more, they spend more, and they tell their friends. This kicks off a positive feedback loop: safety drives growth, and that growth helps fund even better safety initiatives.
This all hinges on three pillars working together seamlessly:
- Clear Policies: These are the laws of your digital city. They need to spell out what's acceptable and what isn't, in a way that’s fair, transparent, and easy for anyone to grasp.
- Proactive Moderation: Think of this as your team of first responders. They enforce the rules using a mix of sophisticated tech and sharp human judgment to spot and handle bad behavior.
- Smart Technology: These are your automated patrol systems—like AI-powered image scanners and fraud detection algorithms—that monitor the platform 24/7, flagging threats before they can spread.
A platform's commitment to safety is a direct reflection of its commitment to its users. Neglecting it is like building a skyscraper on a weak foundation; the collapse is not a matter of if, but when.
The True Cost of Inaction
Pushing trust & safety to the back burner creates problems that are far more damaging than a few bad headlines. When abuse goes unchecked, it poisons the user experience. People lose confidence, they stop showing up, and the platform’s reputation takes a nosedive that can be incredibly difficult to recover from. Just look at the stats: according to the Global Anti-Scam Alliance, a staggering 57% of adults ran into a scam in the last year alone.
Worse, failing to protect your community is an open invitation for regulatory headaches and massive legal fines. Investing properly in T&S isn't just about managing risk; it’s an investment in your platform’s future, ensuring it remains a place where your community can thrive.
The Ever-Shifting World of Digital Threats
If you want to build an effective trust & safety program, you have to know your enemy. The threats we face online aren’t a fixed set of problems; they're a constantly shifting landscape shaped by bad actors who are always finding new ways to exploit platforms and their users. Building a solid defense starts with understanding their tactics.
These threats rarely exist in a vacuum. More often than not, they’re part of a complex chain reaction, starting with something as simple as a misleading post and escalating into real financial damage or personal harm. To stop them, you need to see how the pieces fit together.
What Are We Up Against?
Online threats come in all shapes and sizes, and each one demands a different response. From subtle manipulation to blatant fraud, a good trust & safety team knows how to spot the nuances.
Here are the usual suspects:
- Misinformation and Disinformation: This is the spread of false content. The key difference is intent—misinformation can be an honest mistake, while disinformation is deliberately crafted to deceive people, often for political or financial reasons.
- Scams and Fraud: These are all about tricking people out of their money or personal data. Think of everything from basic phishing emails to incredibly sophisticated "pig butchering" scams that build long-term trust before pulling the rug out.
- Hate Speech and Harassment: This is content that attacks or demeans people based on things like their race, religion, gender, or sexual orientation. It poisons the well, creating a toxic environment that pushes good users away.
- Intellectual Property (IP) Abuse: This covers everything from selling counterfeit sneakers and pirated movies to impersonating a well-known brand to trick customers.
- Synthetic Media and Deepfakes: This is the new frontier of online threats. It involves using AI to create incredibly realistic but entirely fake images, videos, or audio. This tech is a game-changer for spreading disinformation and committing fraud. You can get a deeper dive in our guide on what is synthetic media.
To better understand how these threats operate, let's break down their core components and consequences. The table below provides a quick overview of the most common threat categories, what they look like in practice, and the damage they can cause.
Common Digital Threats and Their Impact
| Threat Category | Description | Impact on Users | Impact on Platform |
|---|---|---|---|
| Mis/Disinformation | Spreading false or intentionally misleading content to deceive or manipulate. | Erodes trust, causes confusion, can lead to real-world harm. | Damages reputation, potential legal/regulatory risk, user churn. |
| Scams & Fraud | Deceptive schemes designed to steal money or sensitive personal information. | Financial loss, identity theft, emotional distress. | Loss of user trust, liability issues, decline in engagement. |
| Hate & Harassment | Content targeting individuals or groups with abuse based on their identity. | Creates a toxic, unsafe environment, causes psychological harm. | Drives away users, brand safety concerns for advertisers, community decay. |
| IP Abuse | Unauthorized use of copyrighted material, trademarks, or counterfeit goods. | Users receive fake products, brand trust is damaged. | Legal liability, loss of legitimate business partners, reputational harm. |
| Synthetic Media | AI-generated deepfakes and other manipulated content used for malicious purposes. | Deception, reputational damage, fraud, political manipulation. | Becomes a vector for all other threats, extreme moderation challenge. |
Understanding these distinctions is the first step. Recognizing that a deepfake video can be used to perpetuate a financial scam is the next. A holistic trust & safety strategy treats the ecosystem, not just the individual symptoms.
The New Age of AI-Powered Attacks
The tools bad actors have at their disposal are getting smarter and faster. Artificial intelligence isn't just a buzzword anymore; it's the engine driving the creation and spread of online threats at a scale we've never seen before.
This puts trust & safety teams in a tough spot. In fact, a recent survey found that 63% of Trust & Safety professionals say "staying ahead of emerging threats" is one of their biggest challenges. That’s a direct response to how quickly AI-generated misinformation and sophisticated new attacks are popping up.
The goal of a bad actor is to exploit trust at scale. They use technology not just to create harmful content, but to make it spread faster than any human team can possibly contain it.
This new reality means the old ways of doing things just aren't enough. Static rulebooks and purely manual content review are like bringing a knife to a gunfight when you’re up against threats that can be generated and deployed in milliseconds.
From Deepfakes to Financial Scams: Connecting the Dots
So, what does this look like in the real world? Imagine a scammer using an AI tool to perfectly clone a CEO's voice. They then use that fake audio in a call to an employee in the finance department, tricking them into wiring company funds to a fraudulent account. This isn't a scene from a movie; it's a real and growing type of corporate crime.
Or think about a political campaign. Bad actors can now spin up thousands of AI-generated social media profiles to blast out a fake news story, complete with convincing deepfake images, to sway public opinion right before an election. The speed and realism can fool almost anyone.
These examples drive home a crucial point: modern digital threats are deeply interconnected. A deepfake video (synthetic media) might be the centerpiece of a cryptocurrency scam (financial fraud), all amplified by a network of automated bot accounts (platform manipulation). To fight back effectively, you have to see how these elements work together. A strong trust & safety program is one that builds a layered defense, ready to spot and neutralize each part of a complex attack.
Building Your Trust & Safety Operations
Think of a top-tier Trust & Safety team as a specialized emergency response unit for your online community. It needs a diverse crew with very specific skills, ironclad protocols for handling whatever comes their way, and a strong support system to keep everyone sharp and healthy. Without this foundation, even the best policies and tech will crumble under pressure.
The real goal is to build an operation that’s both smart with technology and grounded in human judgment. It all starts with getting the right people in the right seats.
Assembling Your Core Team
Just like a hospital needs surgeons, nurses, and lab techs, an effective T&S team requires a blend of strategic thinkers and hands-on experts. Each role is a critical piece of the puzzle.
- Policy Experts: These are the architects of your community's rulebook. They’re tasked with translating broad principles like "be respectful" into clear, enforceable guidelines that leave no room for guesswork.
- Frontline Moderators: Your first responders. They're in the trenches every day, reviewing user-generated content and behavior against the policies you've set. They make the crucial first call on whether something crosses the line.
- Investigators and Escalation Specialists: This is the team that handles the really tough stuff. When a frontline moderator flags a complex or high-stakes case—like a coordinated harassment campaign or a sophisticated fraud ring—these specialists dig deep to uncover the full story.
- Analysts and Data Scientists: This is your intelligence unit. They're constantly hunting for trends in the data, measuring how well your enforcement actions are working, and spotting new threats before they blow up.
These roles work together to tackle a whole spectrum of issues, from subtle misinformation to outright abuse.
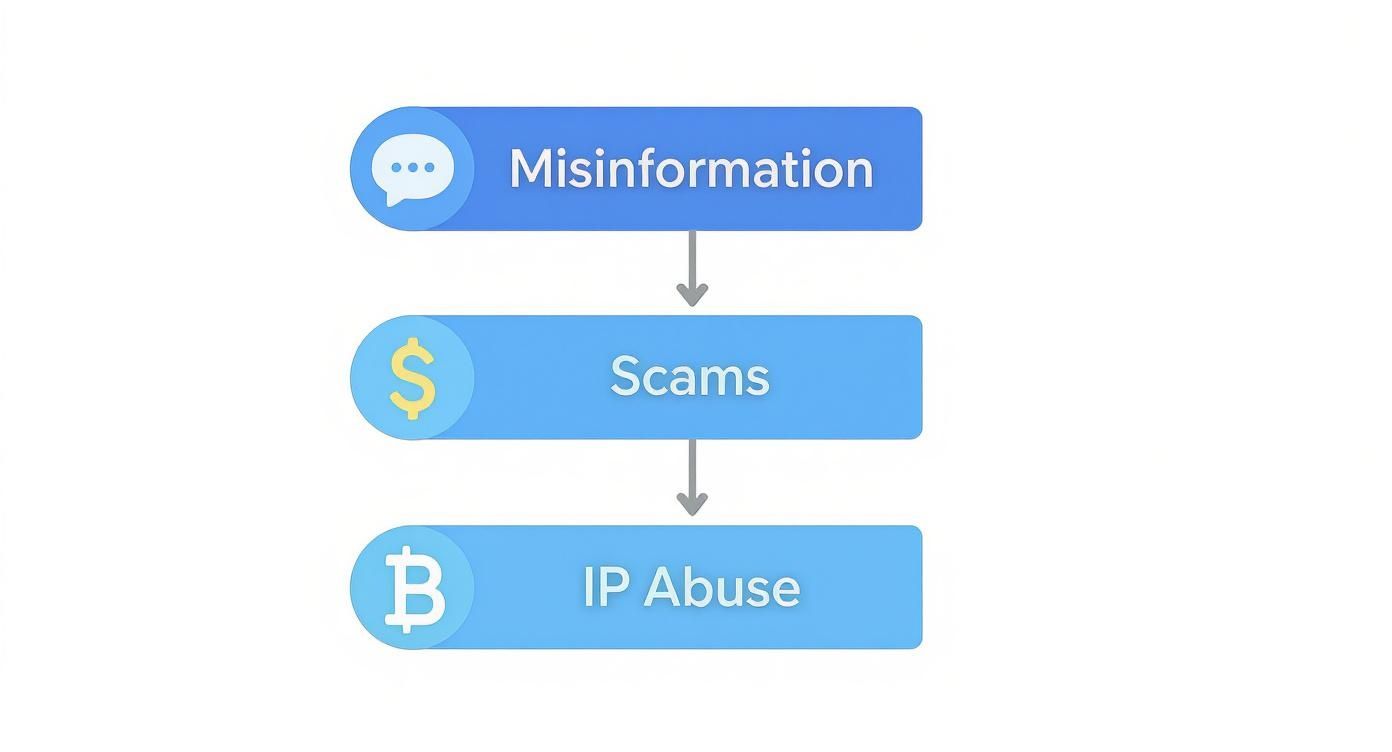
As you can see, what starts as one type of bad behavior can easily escalate into another. This is why you need a team that can connect the dots and handle everything from deceptive content to direct financial harm.
Designing a Seamless Workflow
With your team in place, the next step is building a crystal-clear workflow. This is your operational playbook, detailing exactly how an incident is managed from the moment it's spotted to its final resolution.
- Detection: A potential violation gets flagged. This could happen automatically through an AI model trained to spot spam, or it might come from a user report.
- Triage & Investigation: The flag goes to a frontline moderator who assesses the content. They’ll gather context, maybe check the user's history, and decide if a policy was actually broken.
- Enforcement: Based on the findings, the moderator applies the right penalty. It could be as simple as removing the content and issuing a warning, or it might be a temporary suspension or even a permanent ban.
- Escalation: If a case is unusually tricky, sensitive, or involves a high-profile user, it gets passed up to the specialist team for a deeper dive.
- Appeals: This is non-negotiable. Users need a straightforward way to appeal a decision they feel was wrong. An appeals process is fundamental to fairness and maintaining trust.
A structured process like this is what separates chaos from consistency. It makes every action predictable and accountable. To get a better sense of how this works in practice, you can explore our guide on the role of content moderation services.
A well-defined workflow removes ambiguity. It empowers moderators to act decisively while ensuring that every user is treated fairly under a consistent set of rules.
Prioritizing Moderator Well-Being
Here’s the part that too many companies get wrong: you must provide robust mental health support for your team. This is arguably the most critical component of a sustainable T&S operation.
Your moderators are exposed to the absolute worst of the internet, day in and day out. That constant exposure takes a heavy toll, leading to burnout, secondary trauma, and other serious mental health issues.
Building a resilient team means being proactive about psychological safety. That includes regular wellness checks, easy access to professional counseling, and fostering a culture where people feel safe talking about the emotional weight of their work. In fact, a cornerstone of trust and safety in the workplace is making sure employees feel secure enough to speak up about risks or mistakes.
Investing in your team’s well-being isn't just a nice-to-have—it's a business necessity. A healthy, supported team is an effective team, and that’s what keeps your entire safety operation running for the long haul.
Using Technology for Proactive Defense

Let's be realistic: manual content review alone can’t keep up. The sheer volume and speed of digital content today means that a purely human-led approach is like trying to empty the ocean with a bucket. To build a defense that actually works, trust & safety teams have to shift from a reactive cleanup crew to a proactive force, using technology to spot and neutralize threats before they can spread.
Think of this approach as building a digital immune system for your platform. It’s always on, constantly learning, and spots threats at a scale and speed no human team ever could. Artificial intelligence and machine learning are the heart of this system, acting as a powerful force multiplier for your people.
This isn’t about replacing human experts. It’s about letting technology handle the overwhelming scale of the problem so your team can focus on the nuanced, complex cases that demand real critical thinking. This partnership is what a modern T&S strategy is all about. To get a better sense of what this looks like in practice, check out a guide to automated security remediation and proactive defense.
The AI-Powered Moderation Toolkit
AI isn't a single magic bullet; it's more like a specialized toolkit. Each tool is built for a specific job, trained on mountains of data to recognize the distinct patterns of harmful content. This allows for an incredibly fast and consistent first line of defense.
Here are the key tools you’ll find in the kit:
- Image and Video Recognition: These models are your visual watchdogs. They scan uploads for known harmful imagery, like graphic violence or Child Sexual Abuse Material (CSAM), by matching them against established databases. They're also great at spotting more subtle things, like brand logos used for impersonation or prohibited items in a marketplace listing.
- Natural Language Processing (NLP): NLP is all about understanding text. These algorithms dig into the meaning and sentiment behind words to flag hate speech, harassment, and bullying. They're especially crucial for catching the tricky language used in phishing scams, even when bad actors use slang or coded words to hide their tracks.
- Anomaly Detection: This is your platform’s fraud investigator. Anomaly detection models first learn what "normal" user behavior looks like, then flag anything that veers sharply from that baseline. A sudden flood of new accounts from one IP address, bizarre login patterns, or unusual transaction behaviors are all red flags that can point to scams or account takeovers.
Working together, these systems create a powerful, automated shield that filters out the overwhelming majority of clear-cut policy violations.
The Human-in-the-Loop Model
No matter how smart an AI gets, it will never truly understand human context, culture, or intent. That’s why the human-in-the-loop model is the gold standard in any serious trust & safety operation. It’s where machine speed meets human judgment.
Here’s how it works: AI handles the first pass. It blitzes through millions of posts, images, and videos, flagging potential violations and giving each one a confidence score. This initial triage is brutally efficient, doing in minutes what would take a human team years.
AI excels at identifying the 'what'—the patterns in the data. Human moderators provide the crucial 'why'—the context that determines whether an action is truly a violation.
Content that the AI flags with near-certainty as a violation can be dealt with automatically. But the tricky stuff—items with lower confidence scores or cases that are sensitive or ambiguous—gets routed to a human moderator for the final call. This keeps the system from punishing a user for a sarcastic joke, a culturally specific comment, or something that's edgy but not actually abusive.
This workflow is a game-changer for a few key reasons:
- Massive Scalability: It lets you manage content on a global scale without needing an impossibly large team of moderators.
- Increased Speed: Harmful content is often identified and taken down in minutes, if not seconds, dramatically shrinking its reach and the harm it can cause.
- Improved Moderator Focus: By clearing the table of obvious spam and clear-cut violations, this model frees up your human experts to dig into the gray-area cases that require real investigation.
- Continuous Learning: Every decision a human moderator makes is fed back into the AI models. This feedback loop helps the machine learn from its mistakes, constantly getting smarter and more accurate over time.
Ultimately, this hybrid approach gives you the best of both worlds. You get the tireless vigilance and speed of machines, backed by the essential wisdom, empathy, and contextual awareness that only a human can provide.
Crafting Fair Policies and Consistent Enforcement
Think of your platform’s policies as its constitution. They're the foundational rules everyone agrees to live by. When that constitution is confusing, biased, or applied inconsistently, trust falls apart. This creates a playground for bad actors, while well-intentioned users feel left out in the cold.
Building solid policies is a delicate balancing act. You have to protect your users without stifling their freedom of expression, and you need to write rules that someone from any corner of the world can easily grasp. The real goal is to create a sense of shared understanding, not just a list of things you can't do.
Getting this wrong isn't just a community problem; it's a financial one. A recent PwC’s 2025 Global Digital Trust Insights survey found that 77% of organizations are planning to boost their cybersecurity budgets. With the average data breach now costing an eye-watering US$3.3 million, it’s clear that strong user policies are a critical line of defense.
Designing Your Policy Framework
A good policy framework operates a lot like a fair legal system. It tells people exactly what’s out of bounds and what will happen if they cross the line. Predictability is the name of the game here, because it's what builds confidence and a sense of due process among your users.
Your framework needs a few non-negotiable parts:
- Crystal-Clear Violation Definitions: Vague rules are your enemy. Don't just say "no harassment." Instead, define it with concrete examples of what that looks like on your platform. What words are off-limits? What kind of repeated behavior crosses the line?
- A Transparent Enforcement Ladder: Users need to know what to expect. Map out the consequences, starting with a warning for a first slip-up and escalating to temporary restrictions, account suspensions, and finally, a permanent ban for severe or repeat violations.
- A Robust Appeals Process: Mistakes happen. Moderators are human. That’s why every user needs a straightforward way to appeal a decision they feel was made in error. A fair appeals system is absolutely essential for maintaining trust.
A policy is only as good as its ability to be understood and consistently applied. Ambiguity is the enemy of fairness and the ally of bad actors who exploit loopholes.
To help visualize how this works, a tiered enforcement model is a great tool. It ensures that the response always fits the violation, which is crucial for building a system that users perceive as fair and predictable.
Here is a simple framework for how to structure enforcement actions:
Policy Enforcement Actions Framework
| Violation Level | Example Violation | First Offense Action | Repeat Offense Action |
|---|---|---|---|
| Level 1 | Minor spam, off-topic comment | Content removal & warning | Temporary mute (24 hours) |
| Level 2 | Mild harassment, insults | Content removal & 3-day suspension | 30-day suspension |
| Level 3 | Hate speech, credible threats | Content removal & permanent ban | N/A |
| Level 4 | Illegal content (e.g., CSAM) | Immediate permanent ban & report to authorities | N/A |
By establishing a clear ladder like this, your team can apply rules with confidence and consistency, and your users will understand the "why" behind any action taken.
The Critical Role of Consistency
Consistency is the absolute bedrock of fair enforcement. If the rules apply to some users but not others, you’ve got a massive problem. The perception of bias can be just as corrosive as actual harmful content, as it completely undermines faith in your entire system.
This is where intensive moderator training and clear internal guidelines are so important. Your team needs a shared playbook for applying the rules, no matter who the user is or how popular their account might be. Regularly documenting and reviewing enforcement decisions is key to spotting inconsistencies before they spiral into a bigger issue.
Evolving Policies with Your Community
Finally, remember that your policies can't be carved in stone. They need to be living documents that can adapt over time. New threats will pop up, and your community’s norms will naturally shift.
This is where trust & safety becomes a team sport. Actively engage with your users through surveys, feedback forms, and even community advisory boards. This creates a vital feedback loop that not only helps you write better rules but also makes people feel like they have a real stake in the platform's health. When you make changes, be transparent about why. It reinforces the idea that keeping the community safe is a responsibility everyone shares.
Measuring Success and Navigating Compliance
You can't manage what you don't measure. A trust & safety program without clear goals is just a cost center, constantly reacting to problems. When you have the right data, you can prove your value, justify your budget, and spot new threats before they blow up. It’s how you turn T&S from a necessary expense into a strategic advantage.
But what does success even look like? It's not just about taking down bad stuff. The real goal is to build an environment where people feel safe enough to stick around and engage. To get there, you need a balanced set of metrics that show how efficiently your team is working and how healthy your community actually is.
Key Metrics for Trust & Safety Teams
To get a real sense of how your program is performing, you need to track a mix of metrics that tell you about your team's speed, accuracy, and overall impact on the user experience.
Here are a few of the big ones:
- Time to Action (TTA): How long does it take from the moment a problem is flagged to the moment a human takes action? Every second counts here, so a low TTA is crucial for stopping harm from spreading.
- Moderator Accuracy Rate: What percentage of your team's decisions—like removing or keeping content—line up with your policies? High accuracy means you're enforcing the rules fairly and consistently.
- Prevalence of Violative Content (PVC): This is the holy grail metric. It estimates how much harmful content your users actually see. It's the best way to know if your proactive defenses are truly working.
The ultimate goal of a trust & safety program isn’t to achieve a 100% takedown rate of reported content, but to reduce the overall prevalence of harmful material users encounter in the first place.
These numbers tell a story. If your TTA is creeping up, you might be understaffed. If accuracy dips, maybe your training needs a refresh. Tracking this data lets you make smart, informed decisions. This approach is also critical when working with outside vendors; a solid third-party risk management framework relies on having clear performance data.
Navigating the Regulatory Landscape
On top of your internal goals, you’re also dealing with a tangled web of global laws. Compliance isn't a "nice-to-have"—it's a legal requirement, and ignoring it can lead to massive fines and a shattered reputation.
Major regulations like the EU’s Digital Services Act (DSA) are changing the game for everyone. The DSA, for instance, places heavy demands on platforms for transparency in content moderation, stronger user appeal rights, and mandatory risk assessments.
Staying on the right side of the law means knowing your obligations in every country you operate in. This goes deep into your operational processes, especially when it comes to data privacy and the best practices for handling confidential information.
This isn't something you can figure out on the fly. It takes dedicated legal expertise and adaptable workflows. By building your T&S program with compliance in mind from the start, you not only avoid legal trouble but also show your users that you're serious about accountability.
Common Questions About Trust & Safety
If you're building a trust & safety program from the ground up, or just trying to make sense of it all, you're not alone. Here are a few of the most common questions that pop up, especially when trying to balance ambitious goals with real-world resources.
How Can a Small Team Even Begin to Tackle Trust & Safety?
For startups and smaller teams, the idea of building a T&S function can feel overwhelming. But you don't need a huge department to make a real difference. The trick is to work smart, not just hard. It’s all about being strategic and lean.
Here’s where to start:
- Write Down the Rules: Before you do anything else, create a simple, clear set of community guidelines. Don't use legal jargon; write them so your users and your team can actually understand and apply them.
- Empower Your Users: Your community is often your best first line of defense. Build a reporting system that’s dead simple to use. Make it incredibly easy for people to flag content that feels off.
- Get Help from Automation: You don’t need to build a complex system yourself. Use third-party tools or basic AI filters to catch the low-hanging fruit—the obvious spam and clear policy violations. This frees up your team’s brainpower for the tricky stuff.
Remember, a small, focused team that knows what to prioritize can often outperform a large, disorganized one. Figure out what poses the biggest threat to your specific community and tackle that first.
What’s the Right Mix of AI and Human Moderators?
This is the million-dollar question, and the answer isn't "one or the other." The best T&S operations rely on a “human-in-the-loop” approach, where technology and people play to their strengths.
AI is a beast when it comes to speed and scale. It can sift through millions of pieces of content in the blink of an eye, flagging obvious violations. But humans bring something irreplaceable to the table: context, nuance, and judgment. Machines struggle with sarcasm, cultural context, and borderline cases.
A good rule of thumb is the 80/20 split. Let AI handle the 80% of straightforward cases, allowing your human experts to dig into the complex 20% that actually requires a thoughtful decision. This hybrid model gives you the efficiency of machines without sacrificing the fairness of a human touch.
What Does the Future of Trust & Safety Look Like?
The field is shifting from being reactive to proactive. Instead of just cleaning up messes, the future of trust & safety is about getting ahead of them before they cause real harm.
We're moving toward a world where predictive analytics will help spot risky behavior patterns early on. Advanced AI will become essential for detecting sophisticated deepfakes and other synthetic media.
We'll also see much more cross-platform collaboration. Bad actors don't stick to one site, and neither should our defenses. Companies will increasingly share intelligence to fight coordinated abuse. Ultimately, T&S is becoming less of a backstage janitorial crew and more of a core strategic function that directly shapes product design and builds genuine user trust.
At AI Image Detector, we build tools for the modern trust and safety team. Our technology helps you identify AI-generated content at scale, giving you a critical edge in the fight against misinformation and fraud. Verify your first image for free and see how it works.
