Preventing identity fraud: Essential Tips to Safeguard Your Data
Stopping identity fraud isn’t just about having a strong password anymore. It's about building a multi-layered defense to proactively secure your digital footprint. Think of it as a combination of good digital hygiene—like using unique credentials for every single account and turning on multi-factor authentication—and active vigilance. You have to be the one checking your bank statements and credit reports for anything that looks off. This one-two punch makes you a much tougher target for criminals.
Understanding Modern Digital Identity Threats
The game has changed. We've moved way past the simple phishing emails and stolen passwords that used to be the main concern. Now, criminals are using incredibly sophisticated tools to create fakes that are almost impossible to spot with the naked eye. The old ways of verifying someone—just asking for a photo ID or basic personal info—simply don't cut it anymore.

Today’s fraudsters are using artificial intelligence to cook up synthetic identities. These are entirely new profiles made by mixing real, stolen information with completely fabricated details. They’ll even use AI-generated profile pictures that look shockingly real. These "ghost" identities don't belong to any single person, which makes them a nightmare to trace and shut down.
Fraud doesn’t start when the money is stolen; it starts the moment an identity is stolen or forged. By the time a fraudulent transaction shows up on your statement, the real crime—the identity compromise—is already in the rearview mirror. We have to shift our focus to securing the point of identity creation to truly get ahead of this.
The New Wave of AI-Driven Fraud
The scale of this problem is almost hard to believe. Some projections estimate that identity fraud losses could balloon to $10.5 trillion annually worldwide by 2025, and AI-driven tactics are the main engine driving that growth. These advanced methods are slipping right past the traditional security checks at banks, online stores, and even social media platforms.
For instance, what we call first-party fraud—where someone uses manipulated images to impersonate a legitimate user—has doubled in just one year. It now makes up 36% of all fraud incidents. You can dig into more of the numbers in this comprehensive identity theft report from G2.
This new reality demands a more vigilant and adaptive approach to security. To get started, it helps to know exactly what you're up against.
Modern Identity Fraud Threats and Initial Defense Actions
Here’s a quick rundown of the most common threats we're seeing today and the first things you should do to defend against them.
| Threat Type | Description | Immediate Action |
|---|---|---|
| Synthetic Identity Fraud | Criminals combine real and fake data (e.g., a real SSN with a fake name and AI photo) to create a new, non-existent identity. | Use advanced verification tools to check for digital artifacts in submitted photos and cross-reference data points for inconsistencies. |
| Account Takeover (ATO) | An attacker gains unauthorized access to an existing account using stolen credentials, often from data breaches. | Immediately change your password, enable multi-factor authentication (MFA), and check for any unauthorized activity or changes to your account settings. |
| Deepfake Impersonation | AI is used to create realistic video or audio of a person to deceive verification systems or manipulate individuals. | Be skeptical of urgent, unusual requests, even if they appear to come from a known person. Verify through a separate, trusted communication channel. |
Understanding these specific attack vectors is the first real step in building a defense framework that can actually stand up to today's threats.
How to Fortify Your Personal Digital Defenses
Building a solid defense against identity fraud isn't about finding a single magic bullet. It’s about creating layers of security that work together. While that might sound intimidating, the most effective strategies are usually simple habits and smart setups that make you a much harder target for criminals looking for an easy payday.

This means we have to move beyond just using a strong password. It’s a shift in mindset—being more deliberate about who gets access to your information and more vigilant about the digital doors you might be leaving open.
Implement Smarter Multi-Factor Authentication
Multi-factor authentication (MFA) is one of the most powerful shields you have, but it's crucial to understand that not all MFA is created equal. Getting a code via text message is definitely better than nothing, but it has a known weakness: SIM swapping. This is where a fraudster cons your mobile provider into moving your phone number to a device they control.
A far more secure route is to use an authenticator app or a physical security key. These methods aren't tied to your phone number, which makes them incredibly difficult for thieves to bypass.
- Authenticator Apps: Tools like Google Authenticator or Authy generate a fresh, time-sensitive code on your device itself.
- Physical Security Keys: A small USB device, like a Yubikey, that you plug into your computer or tap on your phone offers the most robust protection out there.
Start by switching your most critical accounts to one of these stronger MFA options—think primary email, banking portals, and any password managers you use. This one change alone dramatically raises the barrier for any would-be attacker.
Become a Phishing Detection Expert
Forget the old days of phishing emails riddled with typos. Today’s scammers use personal details they've scraped from social media or data breaches to craft highly personalized and convincing messages. Their entire strategy is built on creating a sense of urgency to make you act before you think.
Here's a classic example I see all the time: you get a text that looks like it's from a major courier. It says, "Your package delivery has been rescheduled. Please confirm your address and a small redelivery fee at [suspicious link] to avoid return." The link might look almost right, and if you're actually expecting a package, your gut reaction is to click.
The most effective defense against phishing is a moment of strategic hesitation. Before clicking any link or downloading any attachment from an unexpected message, stop and verify the request through a separate, trusted channel.
Don't click that link. Instead, open your browser, go directly to the courier's official website, and pop in your tracking number there. Cultivating this simple habit of independent verification is your best defense against even the most sophisticated phishing attempts.
Conduct Regular Security Checkups
Good digital hygiene isn't a one-and-done task; it requires ongoing vigilance. You can't just set up your defenses and walk away. I always tell people to treat their digital security like a regular health checkup by scheduling a bit of time to review key accounts.
Make it a monthly routine to do the following:
- Scan Bank and Credit Card Statements: Look for any transaction you don't recognize, no matter how small. Fraudsters often "test" stolen cards with tiny purchases to see if they work before going on a shopping spree.
- Check Your Credit Reports: You're entitled to a free credit report from each of the three main bureaus (Equifax, Experian, and TransUnion) every year. A great strategy is to stagger your requests, checking one every four months. You're looking for new accounts or credit inquiries you didn't authorize.
- Secure Your Home Wi-Fi: Make sure your home network is locked down with a strong, unique password and uses WPA2 or WPA3 encryption. Just as important, change the default administrator password on your router itself to block unauthorized access.
By turning these actions into a routine, you build a powerful early-warning system that can catch suspicious activity before it snowballs into a much bigger problem.
Using Advanced Tools to Verify Digital Identities
Technology is a double-edged sword in the fight for digital safety. While fraudsters have powerful tools to create convincing fakes, we can use even smarter tech to catch them. Advanced tools, especially those driven by AI, are your best line of defense against identity fraud, spotting forgeries the human eye would almost certainly miss.

For individuals, this means having a quick way to vet a suspicious social media profile or a seller on an online marketplace. For businesses, it's about building robust validation right into the customer onboarding process to stop fraud before it ever gets a foothold.
These tools are trained to see the invisible fingerprints left behind when a digital image is created from scratch.
How AI Detectors Uncover Fakes
AI image detectors don't just "look" at a photo; they perform a forensic analysis in seconds. They've been trained on millions of both real and AI-generated images, learning to recognize the subtle, almost imperceptible giveaways that generative models often leave behind.
You'd be surprised what they can find. These are some of the most common red flags:
- Unnatural Lighting and Shadows: AI still struggles with how light realistically interacts with a scene. You’ll often see shadows falling in the wrong direction or highlights that just look painted on.
- Pixel-Level Artifacts: The generation process can leave behind digital "noise" or strange, blocky patterns in what should be solid-colored areas. They’re invisible to us but glaringly obvious to an algorithm.
- Bizarre Background Details: Look closely at the background of a suspected fake. You might spot distorted shapes, nonsensical objects, or textures that seem to melt into one another—a classic AI error.
- Symmetry and Proportional Flaws: Sometimes, features like earrings or eyeglasses will be slightly mismatched. Other times, a face might have an eerie, perfect symmetry that you just don't see in real people.
This kind of deep-dive analysis is crucial. Synthetic identity fraud, which involves blending real and fabricated data to create ghost profiles, is a massive problem. Tools like AI Image Detectors expose these fakes by finding hidden inconsistencies, giving you a clear verdict to make an informed decision.
A Real-World Verification Scenario
Let's imagine a common situation. You get a LinkedIn connection request from a potential client. The profile picture looks professional—maybe a little too perfect. Their experience seems legit, but something feels off. How do you confirm they're real in under a minute?
Instead of getting lost in a manual background check, you can use a tool like an AI Image Detector. Just save their profile picture and upload it.
The goal of proactive verification isn't to be paranoid; it's to be prudent. Running a quick check on a digital image is a simple, privacy-safe step that can prevent you from engaging with a fraudulent or malicious account. It’s the digital equivalent of looking through the peephole before opening your door.
Within seconds, the tool gives you a result based on the technical markers it found. It might come back "Likely Human," or it could flag it as "Likely AI-Generated," even pointing out the specific artifacts that led to its conclusion. This gives you a data-driven reason to either accept the connection with confidence or decline it and dodge a potential scam.
This same principle works for businesses verifying government-issued IDs. Our guide on how to spot fake IDs offers a deeper look into the specific visual cues to watch for.
Integrating Verification into Your Workflow
For any business, preventing identity fraud means baking these checks right into your daily operations. Relying on your team to manually review everything is slow, prone to error, and simply can't keep up with the sheer volume of modern digital interactions.
The smart move is to integrate a detection tool’s API for automated verification at key moments, such as:
- Customer Onboarding: Automatically scan submitted ID photos and selfie-style "liveness" checks. This ensures the person creating the account is real and their documents are authentic from the get-go.
- Marketplace Trust and Safety: Let users verify profile pictures or product photos. It's a simple feature that builds a much safer environment for both your buyers and sellers.
- Social Platform Moderation: Quickly flag and remove bot accounts or bad actors who are using AI-generated profiles to spread misinformation or run scams.
To really get a handle on the best practices, it's worth reading more about understanding the nuances of identity verification. By adopting these advanced tools, you shift from reacting to fraud to proactively stopping it, creating a powerful barrier against the growing threat of digital impersonation.
Building a Fraud Prevention Framework for Your Business
Moving from personal security to protecting an entire organization is a whole different ballgame. For a business, stopping identity fraud isn't about one person's safety—it's about weaving a resilient, scalable net that protects every customer, employee, and transaction. It only takes one weak link to jeopardize your whole operation, which is why a structured, multi-layered approach is non-negotiable.
The bedrock of any solid framework is a powerful identity verification (IDV) process. Think of it as the high-tech security at your digital front door. It needs to be strong enough to stop criminals cold before they ever get inside. The trick is to make it seamless for legitimate customers. Too much friction and they'll walk away; too little security and you're rolling out the welcome mat for fraudsters.
Designing a Modern Identity Verification Process
Your IDV process has to be more than just a single checkpoint. Relying on one method, like having someone manually review a driver's license, just doesn't cut it anymore. Today's fraudsters can cook up AI-generated documents that look perfect to the naked eye.
A truly robust process layers different checks together to build a complete identity profile. This means combining things like:
- Document Verification: Using automated tools to scan government-issued IDs for hidden security features, holograms, and data consistency.
- Biometric Analysis: A "liveness check" is a great example. This is where a new user takes a quick selfie or video to prove they're a real person, right there, and not just using a stolen photo.
- Data Cross-Referencing: Ping submitted information against trusted third-party databases to instantly spot any red flags or inconsistencies.
Finding that sweet spot between security and a smooth user experience is everything. If you're exploring solutions to automate and toughen up this critical first step, our guide on the best identity verification software is a great place to start.
Deploying Real-Time Fraud Detection Systems
Getting a customer onboarded securely is just the beginning. The really sophisticated fraud often happens after an account is already active. This is where real-time monitoring, often powered by machine learning, becomes your secret weapon. These systems work quietly in the background, analyzing user behavior for patterns that just don't feel right.
They’re trained to flag suspicious activity that might otherwise go unnoticed, such as:
- A login from an unusual location, especially if it's geographically impossible.
- A flurry of rapid, high-value transaction attempts.
- Sudden changes to core account details, like the registered email or shipping address.
With the explosion of Authorized Push Payment (APP) fraud—where scammers trick people into sending them money—these systems are more critical than ever. Customer expectations are sky-high; 87% in the UK and 83% in the US believe companies should be protecting them from these scams. As a result, businesses are fighting back with AI. A recent global fraud report from Experian found that 76% of firms in EMEA and APAC now use AI and machine learning to spot behavioral anomalies and fake identities.
A winning fraud prevention strategy doesn't just block attacks—it learns from them. Every single attempt you stop, whether it's a synthetic ID at signup or a dodgy transaction, feeds valuable data back into your system. This makes it smarter and better at predicting the next threat.
Choosing the right verification tools depends entirely on your business needs. Here’s a quick breakdown to help you compare the most common methods.
Comparison of Identity Verification Methods for Businesses
An effective identity verification (IDV) strategy balances robust security with a smooth customer experience. This table breaks down common methods to help you decide which approach, or combination of approaches, fits your business best.
| Verification Method | Security Level | User Friction | Best Use Case |
|---|---|---|---|
| Manual Document Review | Low | High | Small-scale operations where speed isn't a priority and fraud risk is low. |
| Database Checks | Medium | Low | Quickly verifying basic customer info like name, address, and age. |
| AI Document & Liveness Check | High | Medium | Financial services, e-commerce, and any platform needing strong proof of identity. |
| Biometric Authentication | Very High | Low (after setup) | Securing ongoing access to high-value accounts or sensitive company data. |
Ultimately, the strongest defense often involves a mix of these methods, tailored to the specific risks you face at different points in the customer journey.
The Human Element: Your First Line of Defense
Finally, never forget the people on your team. You can have all the best technology in the world, but social engineering attacks often bypass it completely by targeting your employees. This is why continuous training isn't just a compliance task to check off a list; it's a vital, ongoing part of your defense.
Your staff needs to know exactly how to spot and handle threats like:
- Phishing and spear-phishing emails designed to steal company credentials.
- Pretexting calls where a fraudster poses as a confused customer or an urgent vendor.
- Internal threats, whether they come from a disgruntled employee or just an accidental mistake.
When you pair strong technological controls with a sharp, well-trained workforce, you create a defensive ecosystem that is exponentially harder for criminals to breach. This holistic mindset is the real key to preventing identity fraud at scale.
What to Do Immediately When Fraud Occurs
That sinking feeling when you realize you're a victim of identity fraud is brutal. It's a personal violation that can send anyone into a spiral of panic and helplessness. But what you do in those first few moments is absolutely critical. A fast, decisive response can make a world of difference, limiting the fallout both financially and emotionally.
Your first priority is containment. You need to build a wall between the fraudster and your assets, and you need to do it now. This isn't a time to second-guess yourself; it's time for methodical, rapid action. Think of it as digital first aid—the quicker you act, the better the outcome.
Your Personal Incident Response Plan
When your personal information gets compromised, the clock starts ticking. The immediate goal is to make your stolen identity as useless as possible to the criminals who have it. This means systematically locking down your credit and alerting the right authorities to get your case on the books.
Here are the essential first moves:
Place a Fraud Alert or Credit Freeze: Get in touch with one of the three major credit bureaus—Equifax, Experian, or TransUnion. The good news is, by law, once you notify one, they have to tell the other two. An initial fraud alert lasts for one year and flags your file so businesses have to verify your identity before opening new credit. For even stronger protection, go for a credit freeze, which blocks access to your credit report almost entirely.
File an Official Report: Head straight to IdentityTheft.gov, the Federal Trade Commission's (FTC) official resource. Filing a report here is a crucial step. It creates an official record of the crime and gives you a personalized recovery plan and the documentation you'll need for what comes next.
Contact Your Financial Institutions: Pick up the phone and call the fraud departments at your bank, credit card companies, and anywhere else you have accounts. You'll need to close any compromised accounts and dispute fraudulent charges—be sure to follow up in writing.
This three-pronged approach throws up immediate roadblocks that can stop a fraudster dead in their tracks.
The Business Response to a Breach
For a business, a fraud incident isn't just a financial problem; it's a full-blown crisis of trust. The response has to be just as swift, but the focus shifts to isolating the breach, protecting customers, and meeting legal duties. A fumbled, disorganized reaction can amplify the damage in a heartbeat.
The single most important action after a breach is transparent communication. Hiding or downplaying the incident erodes customer trust far more than the breach itself. A clear, honest, and empathetic message is your best tool for retaining your customer base and protecting your brand's reputation.
When fraud hits your organization, you need a playbook. To effectively handle security breaches and mitigate damage, it's essential you're already building a robust incident response plan that outlines clear roles and responsibilities before a crisis occurs.
This infographic lays out the core pillars of a proactive business fraud prevention process, focusing on verification, training, and detection.
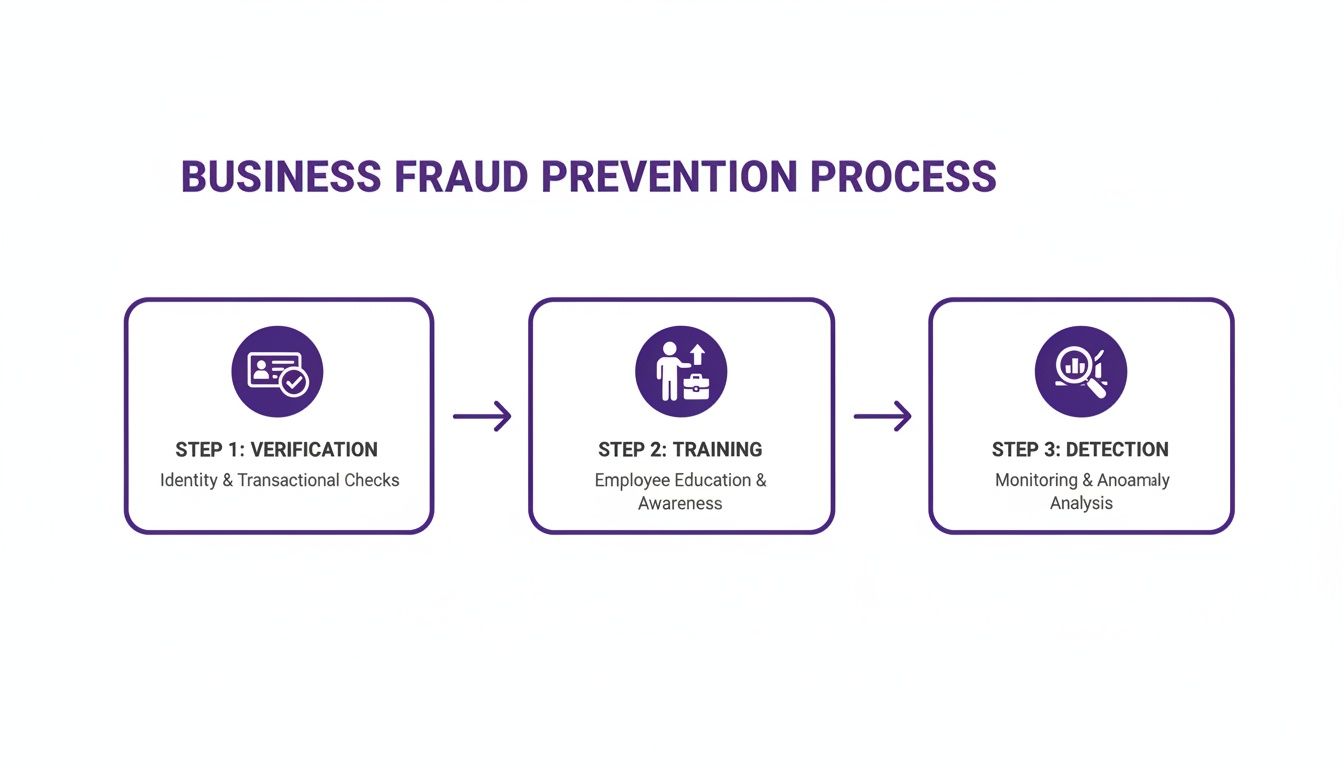
As you can see, a strong defense is built in layers. It all starts with solid identity verification, which is then backed up by continuous employee training and real-time detection systems.
The investigation that follows a breach can get incredibly technical and complex. To get a sense of the technical hurdles involved, you can learn more about the challenges in digital forensics.
Your corporate response plan absolutely must cover these key areas:
- Isolate the System: Get affected systems offline immediately to stop the bleeding and prevent further data loss.
- Notify Affected Parties: Tell your customers, employees, and stakeholders what happened. Be clear, be prompt, and let them know what you're doing to fix it.
- Report to Authorities: Depending on the scale and type of breach, you might be legally required to report the incident to law enforcement or regulatory agencies.
Whether it's personal or professional, a calm, structured, and speedy response is your most powerful asset in the aftermath of identity fraud.
Frequently Asked Questions About Identity Fraud
When you're trying to get a handle on identity fraud, a lot of questions pop up. Even with a good plan in place, the details can get confusing. Here are some clear, straightforward answers to the questions I hear most often.
The goal here is to cut through the noise and give you information you can actually use, whether you're trying to protect your own information or secure your entire business.
How Can I Spot a Fake Profile Picture Without a Tool?
While an AI detection tool is your best bet for accuracy, you can definitely train your eye to catch the obvious fakes. The trick is to look for the little things that generative AI consistently messes up.
Start with the background. Is it a blurry, nonsensical mess? Do objects seem to be melting into each other? That’s a classic sign. Then, zoom in on the person. Look for bizarre details in the hands, ears, or hair. AI often struggles with things like:
- Unnatural shadows or lighting that doesn't fit the scene.
- Perfectly symmetrical faces, which are incredibly rare in real life.
- Mismatched or weirdly shaped earrings.
- An overly glossy, airbrushed skin texture that looks more like a video game character than a person.
One of the most powerful manual checks is a simple reverse image search. Drop the picture into Google Images. You’ll quickly find out if it’s a stock photo or, worse, a picture swiped from someone else's real social media profile.
What Is the Difference Between Synthetic Fraud and Identity Theft?
This is a really important distinction, because you're dealing with two completely different kinds of threats.
Traditional identity theft is exactly what it sounds like. A criminal steals a real person's complete identity—name, Social Security number, the works—and simply impersonates them. In this scenario, there's a real, identifiable victim who will eventually notice something is wrong.
Synthetic identity fraud, on the other hand, is much more insidious. The fraudster plays digital Frankenstein, stitching together bits of real and fake data to invent a brand-new, non-existent person. They might use a real, stolen SSN but pair it with a made-up name and an AI-generated profile picture.
The real danger with synthetic identities is that there's no single person to report the crime. Since the identity is a "ghost," it can exist for months or even years, building a credit history and racking up debt before anyone notices.
These synthetic profiles are built from the ground up to fool automated verification systems, making them a huge headache for financial institutions and other businesses.
Is Freezing My Credit Really That Important?
Yes. It's probably the single most powerful action you can take to prevent new account fraud.
Think of a credit freeze as a digital deadbolt on your financial life. It locks down your credit reports, making it nearly impossible for a thief to open a new credit card, get a loan, or establish any line of credit in your name because lenders can't access your file to approve the application.
Sure, you’ll have to temporarily "thaw" your credit when you need to apply for something yourself, but that process is quick and easy. For the peace of mind it provides, it's a tiny inconvenience. It's a free, incredibly effective tool that puts you back in control.
Do Small Businesses Really Need Advanced Fraud Tools?
Absolutely. I'd argue they need them more than giant corporations.
Fraudsters often see small businesses as easy pickings. They assume you don't have the same robust security measures as a big bank, making you a low-risk, high-reward target. A single major fraud incident can be devastating, wiping out your profits and shattering the trust you've built with your customers.
Investing in modern, affordable tools isn't just an expense; it's essential for survival. This doesn't have to be complicated. Simple, scalable solutions can make a world of difference:
- Use an AI image detector to check customer-submitted IDs during account creation.
- Implement strong, phishing-resistant multi-factor authentication (MFA) for all employee accounts.
- Turn on real-time transaction monitoring to flag activity that doesn't look right.
These measures do more than just protect your bottom line. They safeguard your customers' data and preserve the hard-earned reputation of your brand.
Ready to stop fraud at the source? AI Image Detector gives you the power to instantly verify digital identities and spot sophisticated fakes before they cause harm. Protect your platform, secure your onboarding process, and build trust with your users by trying our free tool today at https://aiimagedetector.com.
